Next remote access VPN I would like to work with is SSL VPN
clientless on ASA. The biggest advantage of this version is lack of
software on client machines, you only need internet browser.
Minimum configuration required is very simple:
and now we can test it:
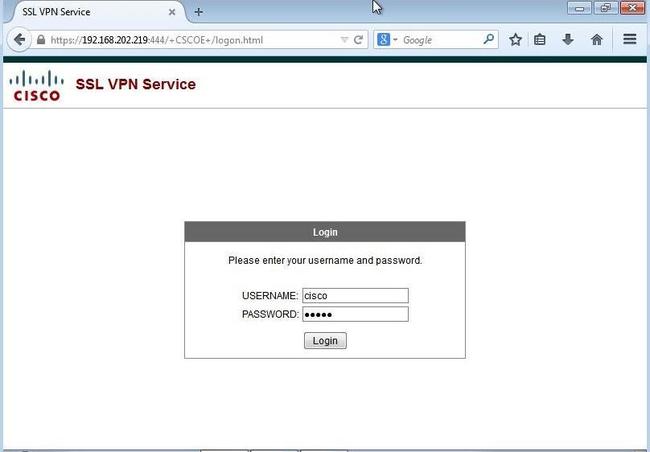
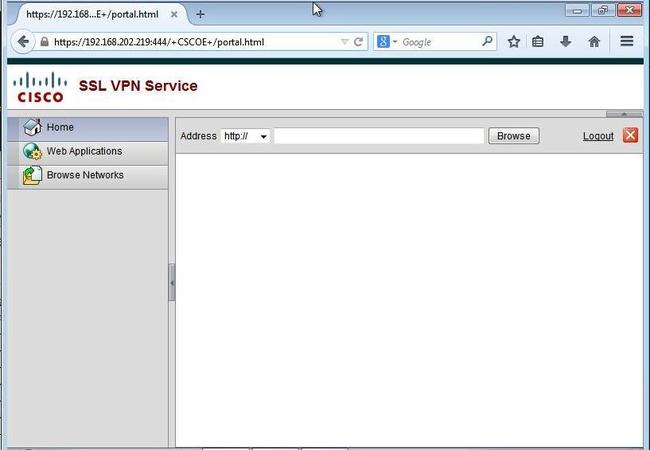
On the ASA we can also monitor this session:

As you see the ping is not allowed on the outside interface and we can’t ping this host.

I enabled http server on R15.


To secure web based application is straightforward. For other types
application we can use Port Forwarding (legacy) and Smart Tunnel. More
information about both you can find here:
a) Port Forwarding: http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/webvpn.html#wp1291474
b) Smart Tunnel: http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/webvpn.html#wp1218044
I pasted documentation from 8.2 version because the one I’m working on (8.4) doesn’t include CLI, only gui.
webvpn
port 444
enable outside
username cisco password cisco
username cisco attributes
service-type remote-accessand now we can test it:


asa1# sh vpn-sessiondb webvpn
Session Type: WebVPN
Username : cisco Index : 16
Public IP : 192.168.202.237
Protocol : Clientless
License : AnyConnect Premium
Encryption : RC4 Hashing : SHA1
Bytes Tx : 7367 Bytes Rx : 12748
Group Policy : DfltGrpPolicy Tunnel Group : DefaultWEBVPNGroup
Login Time : 12:50:22 UTC Thu Dec 11 2014
Duration : 0h:04m:55s
Inactivity : 0h:00m:00s
NAC Result : Unknown
VLAN Mapping : N/A VLAN : none
asa1# 
As you see the ping is not allowed on the outside interface and we can’t ping this host.
asa1(config)# sh run access-list OUT
access-list OUT extended permit icmp any host 9.9.9.9
asa1(config)# 
I enabled http server on R15.


a) Port Forwarding: http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/webvpn.html#wp1291474
b) Smart Tunnel: http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/webvpn.html#wp1218044
I pasted documentation from 8.2 version because the one I’m working on (8.4) doesn’t include CLI, only gui.
Comments
Post a Comment